Potential Threats
| Provide an overview of potential internal and external security threats to an organisation. |
|---|
|
Possible Internal Threats Leakers leaking private information, eg. an employee leaking information about an upcoming game or dlc. Staff spoiling upcoming entertainment such as movies, TV shows and games. Employees downloading viruses to computers. Possible External Threats Theft of data Vandalism of infrastructure Weather Errors from clients |
| What is meant by “Access causing damage”? Your answer to this must include real examples. |
|---|
|
Access causing is a threat created by a hacker that has damaged the system, whether that's internal or external. Internal is damage to data or software inside the system. Planting a virus: In 2013 NBCs website was hacked and malicious code was implemented into the site. The code redirected users to websites that contained the Citadel Trojan. |
| What is meant by “Access without causing damage”? Your answer to this must include real examples. |
|---|
|
Access without causing damage means to gain access to a system but without altering anything. Examples maybe: Espionage: viewing files to know what is going on or what's being planned. - In 1998 a series of cyber attacks resulted in thousands of documents being stolen. These documents contain confidential information on the American military technologies. Theft: stealing data such as passwords - Sony had a network breach in 2011 where users had their usernames, passwords and emails stolen along with other data. Sony was fined £250,000. |
| Explain identity theft and the implications of it. |
|---|
|
Identity theft is when someone poses as someone else or steals their sensitive data. This then leads on to criminal activity. An example of this is when someone's username and password are stolen and purchases are made with their account and they are charged for it. Effects of Identity Theft: - Financial Loss - money could be stolen from accounts and the victim could be less penniless and ruin their credit score. - Struggle Finding Jobs - As well as checking criminal history employers also look at credit scores of employees, if its too low the victim may be denied the position. |
| Explain what the term “Phishing” means and evaluate the impacts it has. |
|---|
|
Phishing is when an email-bourne attack is sent to a recipient and they are tricked into clicking on malicious links that download malware or disclosing private information such as credit card details. Impact 1: Software that can corrupt data on a device or take over the system can be downloaded. Impact 2: Attackers can trick victims into giving card details or login details. This can lead to the attacker using their personal funds. |
| Using examples, explain what website defacement is. |
|---|
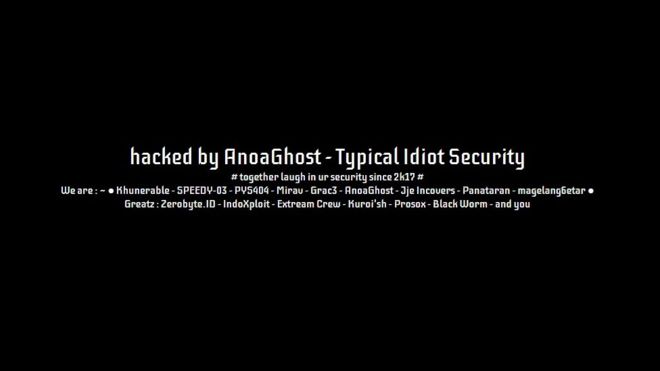
In 2018, a hacker known as AnoaGhost changed the appearance of the NHS website for several days. It had a black background, music and a message was left in white text. |
| What is meant by “Denial of Service Attacks”? Provide examples. |
|---|
|
A denial of service attack is when a system is being overloaded with requests causing it to crash. GitHub - On 28 February 2018, GitHub was attacked by a denial of service attack. The amount of traffic clocked in at 1.35 terabits per second. U.S BanksIn 2012, 2 U.S banks were attacked by a string of DDOS attacks. The traffic floods were for more than 60 gigabits per second. |
| For all of the above cyber security issues, explain with examples the measures that can be put in place to minimise or eliminate the threats. |
|---|
|
Identity Theft 1 - Don’t save passwords to your devices, and don’t log into sites while using on public networks. 2 - Use different passwords on different sites, because if you are compromised on one site then its limited to that site because they don't know your passwords for others. 3 - Regularly check if websites you use have been compromised, e.g - haveibeenpwned.com/ Phishing 1 - Don’t give details to anyone that requests them. Companies don’t ask for personal details such as passwords. Most likely for confirmation, usually to deal with a request from you, they will ask for details on last purchases. 2 - If rewards sound too good to be true it usually is. So when an email comes through about getting a large sum of money it's usually phishing. 3 - Don’t click on shortened links, shortened links hid the websites real name and can take you to malicious sites. Website Defacement 1 - Install a website scanner that can examine your website for malware, it does this in regular intervals. 2 - Scan your source code if you can read the scripts used, particularly look for iframe elements and the URL that follows. 3 - Limit access towards users to allow them to do the things they are allowed to do, blocking them from having access to edit the websites files. Denial of Service Attack 1 - Block IP addresses that have a large amount of traffic coming in. 2 - Installing software, such as firewalls, to monitor your systems to detect any incoming attacks. 3 - Create and use a DDOS response plan to reduce the damage that is made during an attack. |